Table of Contents
Background
WHM/cPanel has the excellent MTA called Exim. The default settings are pretty good for keeping SPAM away, but every now and again a particularly conniving spammer will find a way around your defences. This article was created based on incident of spamming on Exim on WHM. As a bonus we’ve also included a section on how to monitor your Exim mail queue with SNMP.
For the spamming case, the spammer triggered the emails slowly so as to avoid detection. Most of them had dating site messages, some quite suggestive about nude pictures. The text of each message was cleverly altered so as to avoid obvious repeat patterns, e.g. one would have “She might really like you” whereas another would say “She may really be fond of you”. You get the point.
The aim of the first part of this article is to document a list of commonly used command to delete messages in the Exim queue.
Deleting based on body text
grep -lr 'the attached pictures' /var/spool/exim/input/ | sed -e 's/^.*\/\([a-zA-Z0-9-]*\)-[DH]$/\1/g' | xargs exim -Mrm
Replace the attached pictures with your search text.
Deleting based on sender
Typically one would delete based on sender in the Mail Queue management area of WHM, but if you spammer has spoofed the FROM: address you need to do manual work in the queue. Here is one command that will get rid of a message based on the sender (-f):
exiqgrep -i -f [email protected] | xargs exim -Mrm
The caveat is the sender might appear as a spoofed address and you might have to delete the spoofed address instead.
Deleting based on recipient
exiqgrep -i -r [email protected] | xargs exim -Mrm
Anatomy of the above exiqgrep command
Exiqgrep is like grep but just for the Exim queue
-i means return messages IDs only
-f is the sender’s address
The output is then piped (|) to the exim removal command
– Mrm This option requests Exim to remove the given messages from the queue
SNMP Monitoring of the Exim Queue
You can use an SNMP monitoring system such as PRTG and a CRON to create a numeric indicator every minute of the mail queue length. With PRTG you can then set threshold to warn you when the queue gets abnormally large. We typically set three warnings, spread apart. Be warned though that is the queue is breached extremely quickly all three warnings might be triggered in at once, giving a summarized view which doesn’t make the alert obvious. On our systems we actually have two queue monitors due to the devastation that a breached queue causes with polluted IP addresses.
The CRON
The CRON must be installed to point to a stable and permanent site on your server, e.g.:
* * * * * /bin/sh /home/example/public_html/exim/exim.sh
The Script
The script is pretty simple and contains the following lines:
cat /home/example/public_html/exim/exim.sh #!/bin/bash echo "[`/usr/sbin/exim -bpc`]" > "/home/example/public_html/exim/eximqueue.txt"
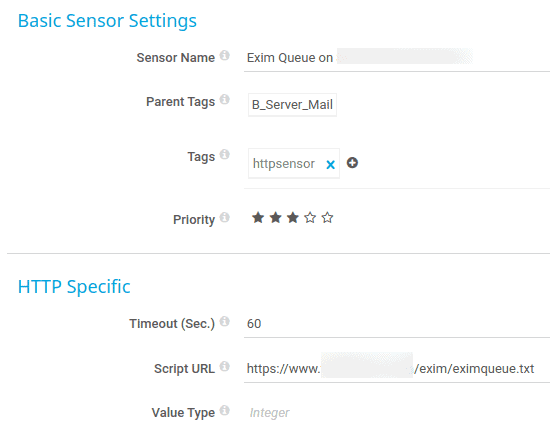
PRTG Setup
In PRTG you’ll be using the HTTP Value Sensor with the default set of Integer:
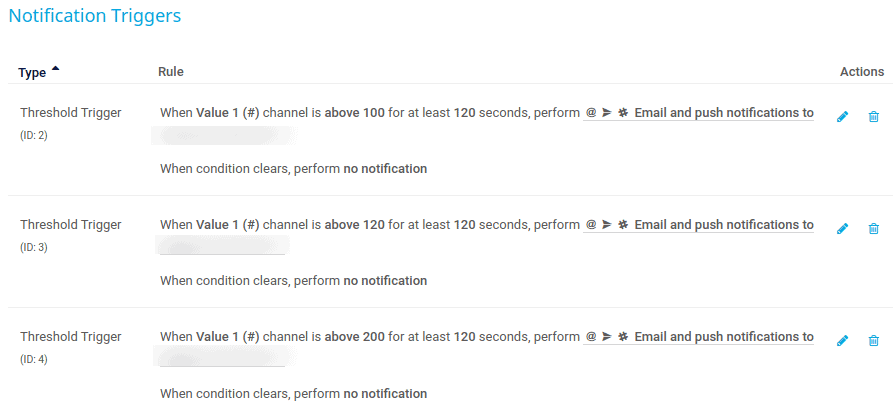
PRTG Notifications Setup
Here is an example of notifications. These ones are set very high for a very busy email server that often has things queued. Other values might be 10, 50, 200, or 5, 20, 100, or 100, 200, 500. You’ll have to decide what is acceptable based on your ability to examine the queue at short notice. For something like a billing system you might want to have it extremely low so as to catch bounces or invalid email addresses to paying clients.
References
- http://bradthemad.org/tech/notes/exim_cheatsheet.php
- https://serverfault.com/questions/571539/how-to-remove-all-messages-from-exim-mail-queue-from-a-certain-user-email
- https://www.exim.org/exim-html-current/doc/html/spec_html/ch-the_exim_command_line.html
- https://www.cyberciti.biz/faq/exim-remove-all-messages-from-the-mail-queue/
- https://www.2daygeek.com/how-to-remove-the-messages-from-exim-mail-queue/