Table of Contents
WordPress Is a Security Hole
WordPress is a convoluted mess of security holes. Every year millions of WordPress websites are attacked because of the poor security provided by the vendor (WordPress.org and the open-source community). You would think some important and core things would have been eliminated by now, but no such luck. The reason why is because WordPress is old and super flexible with it’s plugin system, but with all this flexibility comes a number of difficult to fix holes.
To avoid most of these attacks, you just need to approximately follow the following playbook, roughly ordered from important to less important:
- Update WordPress plugins religiously
- Update WordPress themes religiously
- Update WordPress core
- Disable themes not in use
- Keep PHP up to date
For most savvy hosts and conscientious well-connected hosting clients, this is now common knowledge. But unfortunately the vendor, namely Matt of WordPress.org and it’s open source community, still haven’t been able to fix one particular bad attack, the infamous:
XML RPC Attack
xmlrpc.php is by far one of the most common attacks and the sheer number of attempts to breach it will bring a server’s performance down to it’s knees and cause huge CPU spikes; for minutes, for hours, and sometimes for days on end. In some cases where RAM and / or CPU cycle resources are minimal, the server will quickly get overwhelmed and stop serving efficiently.
Here is an example of an attack (and the eventually subside, which inevitably happens):

This server’s load normally hovers between 1 and 2. As you can see the attack that lasted almost 6 hours took massive CPU cycles. Happy clients? No. Shared hosting is cheap? There is a reason.
Disabling via Plugins
Simple SSL has good documentation on this problem:
How to find the attacked sites
WHM Script
This script will count sites which have had over 4000 entries of the attack vector. Adjust the 4000 up or down.
grep -r "xmlrpc.php" /usr/local/apache/domlogs/ | awk -F: '{count[$1]++} END {for (file in count) if (count[file] > 4000) print file, count[file]}'
When you start cleaning up your server, reduce it to 200:
grep -r “xmlrpc.php” /usr/local/apache/domlogs/ | awk -F: ‘{count[$1]++} END {for (file in count) if (count[file] > 200) print file, count[file]}’
At 200 you’re probably okay. But are you? Do you want perfection? Read on.
Explanation what script does
This server examines the web server’s log files. If you are a sysadmin we use something like this on Virtualmin:
tail -f /home/username/logs/access_log
On cPanel, the location is different but the same. It will become immediately evident if there is a problem because the XML RPC attackers are relentless and attacks every few seconds. Every fucking split second at times. However, tailing is very hard when there are many entries. So use our powerful Bash script instead.
You’ll see something like this:
18.141.236.244 - - [14/Jan/2025:06:33:46 +0200] "POST //xmlrpc.php HTTP/1.1" 200 4207 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0 Safari/537.36" 18.141.236.244 - - [14/Jan/2025:06:33:48 +0200] "POST //xmlrpc.php HTTP/1.1" 200 4207 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0 Safari/537.36" 18.141.236.244 - - [14/Jan/2025:06:33:50 +0200] "POST //xmlrpc.php HTTP/1.1" 200 4207 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0 Safari/537.36" 18.141.236.244 - - [14/Jan/2025:06:33:52 +0200] "POST //xmlrpc.php HTTP/1.1" 200 4207 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0 Safari/537.36"
Note the double //, which is a common pattern. Fuck those assholes, I want automation and these bloody security problems keep me up at night.
Quick Fix for Apache
If you have Apache and you want to do manual protection, follow this routine. Otherwise with WHM use the WP Toolkit which has a convenience menu for this exact threat. To manually fix the problem on Apache, add this to an existing .htaccess file:
<Files xmlrpc.php> Order Allow,Deny Deny from all </Files>
The results are immediate when saving the file. You’ll see something like this when you’re tailing, note the 200s and then the 403.
18.141.236.244 - - [14/Jan/2025:06:53:54 +0200] "POST //xmlrpc.php HTTP/1.1" 200 4040 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0 Safari/537.36" 18.141.236.244 - - [14/Jan/2025:06:53:55 +0200] "POST //xmlrpc.php HTTP/1.1" 200 4040 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0 Safari/537.36" 18.141.236.244 - - [14/Jan/2025:06:53:57 +0200] "POST //xmlrpc.php HTTP/1.1" 403 3806 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0 Safari/537.36"
I like putting this snippet at the top of the file, you know, in case something within WordPress stops working, for example, a plugin that needs access to XMLRPC.
What we find interesting about using this technique on multi-server is you’ll see suddenly that other sites also stop getting attacked. What do you know. On GitHub there is a script to quickly deduce all shared sites on a server and these bored idiot then attack in mass.
Warning about xc2\xa0 characters?
If you get this:
[Thu Jan 23 09:12:31.661189 2025] [core:alert] [pid 833252:tid 140208492889856] [remote a.b.c.d:50104] /home/username/public_html/.htaccess: Invalid command '\xc2\xa0', perhaps misspelled or defined by a module not included in the server configuration, referer: https://example.com/
You copied invisible non-breaking space characters as \xc2\xa0 is the Unicode for a non-breaking space! To find them all do this:
grep -lri "invalid command" /var/log/virtualmin
Quick fix for Nginx
Inside the server block:
location = /xmlrpc.php { deny all; access_log off; log_not_found off; }
Reload nginx afterwards, service nginx reload.
Server wide fix for Apache on Virtualmin
The script
for htaccess in /home/*/public_html/.htaccess; do if [ -f "$htaccess" ] && ! grep -qi 'xmlrpc\.php' "$htaccess"; then # Backup original file cp -p "$htaccess" "${htaccess}.bak" # Prepend xmlrpc block tmpfile=$(mktemp) { echo '<Files xmlrpc.php>' echo 'Order Allow,Deny' echo 'Deny from all' echo '</Files>' echo cat "$htaccess" } > "$tmpfile" && mv "$tmpfile" "$htaccess" # Set correct ownership and permissions user=$(basename "$(dirname "$(dirname "$htaccess")")") chown "$user:$user" "$htaccess" chmod 644 "$htaccess" echo "Updated and fixed: $htaccess (Backup: ${htaccess}.bak, Owner: $user:$user, Permissions: 644)" fi done
Server wide fix for Nginx on Virtualmin
There is none. You have to include that file in every server block!
Mitigating XML RPC using WP Toolkit on a WHM Server
Fortunately WHM has software called “WP Toolkit” which addresses this issue. Below we have identified a server that might get compromised due to this and the advice that “WP Toolkit” on a WHM server suggests:
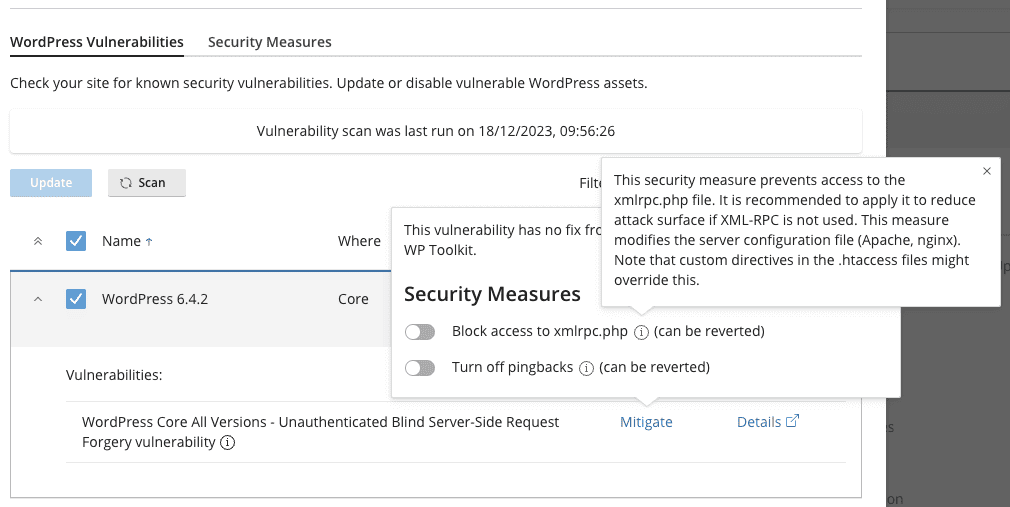
Take note the fine print:
This security measure prevents access to the xmlrpc.php file. It is recommended to apply it to reduce attack surface if XML-RPC is not used. This measure modifies the server configuration file (Apache, nginx). Note that custom directives in the .htaccess files might override this.
Also
This vulnerability has no fix from the vendor yet. It can be mitigated by WP Toolkit.
What does this fix do?
- Blocks access to
xmlrpc.php
What is this fix called?
WordPress Core All Versions – Unauthenticated Blind Server-Side Request Forgery vulnerability
But what if the site breaks and what if I actually use xmlrpc.php?
xmlrpc.php is a fundamental part of quite a few plugins and APIs. It’s beyond the scope of this article to advise what to do if turning off xmlrpc breaks your website. As with many things IT, application is best, testing, and reverting where need.
To the author of this article who has mitigated 100s of xmlrpc attacks it appears WordPress has an architectural problem with that file and they haven’t been able to address it, sadly.
How does this fix work?
Apache’s .htaccess file and NGinx‘s equivalent is updated to avoid this problem.
How to check WHM sites in bulk
Use the following Bash script to check sites in bulk on a WHM server.
Modify the 8000 values to your desired quantum.
grep -r "xmlrpc" /usr/local/apache/domlogs/ | awk -F: '{count[$1]++; last[$1]=$0} END {for (file in count) if (count[file] > 8000) print file, count[file], "matches\nLast match:", last[file]}'
Yep, you read that here first. Some sites will have over 8000 attack lines in the log file.
grep -r "xmlrpc.php" /usr/local/apache/domlogs/ | awk -F: '{count[$1]++; lines[$1]=lines[$1]"\n"$0} END {for (file in count) if (count[file] > 8000) print lines[file]}'
This morning I checked a really busy server. Load was hovering around 14. The command took well over 2 minutes to complete. I ended up deleting all the log file to keep my sanity.
How to check Virtualmin sites in bulk
A variant of the WHM command will scan the Virtualmin logs directory instead:
grep -r "xmlrpc.php" /var/log/virtualmin/ | awk -F: '{count[$1]++; lines[$1]=lines[$1]"\n"$0} END {for (file in count) if (count[file] > 8000) print lines[file]}'
Which well known WordPress plugins use XMLRPC
BEWARE: The following information was obtained form ChatGPT on the 14th of January 2025, so double check the facts. But in essence it gives a good overview where disabling XML RPC might pose some risks.
XML-RPC in WordPress is an API that allows remote interaction with a WordPress site, enabling actions such as posting content or managing settings. While XML-RPC has largely been replaced by the REST API, several well-known plugins still utilize XML-RPC or have done so historically. Here are some examples:
Plugins That Use or Support XML-RPC
1.Jetpack
•Purpose: Connects a WordPress site to WordPress.com for advanced features.
•Use of XML-RPC: Jetpack heavily relies on XML-RPC for its communication between WordPress.com and the site, including features like Site Stats, Related Posts, and automated sharing to social media.
•Note: Jetpack has shifted many functionalities to REST API in newer versions but still supports XML-RPC for compatibility.
2.WordPress Mobile Apps
•Purpose: Official WordPress apps for iOS and Android use XML-RPC to allow posting, media uploads, and comment moderation from mobile devices.
•Use of XML-RPC: It facilitates the remote management features of the app.
3.WooCommerce (Older Versions)
•Purpose: E-commerce functionality.
•Use of XML-RPC: Earlier versions of WooCommerce plugins allowed external systems to manage inventory or orders via XML-RPC.
•Note: WooCommerce now emphasizes REST API for these tasks.
4.IFTTT and Zapier (WordPress Integrations)
•Purpose: Automation tools like IFTTT (If This Then That) and Zapier can use XML-RPC to create workflows that integrate with WordPress, such as posting content from other platforms.
•Use of XML-RPC: Trigger-based actions like auto-publishing posts from RSS feeds or social media.
5.Remote Publishing Plugins
•Examples:
•Blogger Importer Extended
•XML-RPC Plugins for API Integration
•Purpose: Allow remote management and posting from third-party applications or platforms.
•Use of XML-RPC: They leverage XML-RPC to communicate with WordPress for publishing and editing content.
6.Backup and Migration Plugins
•Examples:
•UpdraftPlus
•Purpose: Backup and restoration functionality.
•Use of XML-RPC: Some older versions of backup plugins used XML-RPC for remote backup triggers or cloud service integration.
Security Concerns with XML-RPC
XML-RPC can be vulnerable to brute-force attacks, DDoS amplification, and other security issues if not properly secured. Many plugins and site administrators disable XML-RPC entirely or use security plugins like Wordfence or iThemes Security to monitor and restrict its use.
If you’re using a plugin that relies on XML-RPC, ensure it is necessary for your use case and that your WordPress installation is up-to-date to avoid potential vulnerabilities.